What Is Log Data In Cyber Security are a versatile service for any individual aiming to create professional-quality papers quickly and conveniently. Whether you need personalized invites, resumes, organizers, or calling card, these layouts enable you to customize web content with ease. Just download the design template, modify it to match your demands, and publish it at home or at a printing shop.
These themes save money and time, supplying a cost-efficient option to working with a designer. With a large range of styles and styles readily available, you can locate the excellent style to match your individual or service demands, all while preserving a sleek, expert look.
What Is Log Data In Cyber Security

What Is Log Data In Cyber Security
Do Not Disturb Sign Download Post this laminated sign to keep halls quiet during big tests Check out our do not disturb sign printable selection for the very best in unique or custom, handmade pieces from our signs shops.
Do not disturb sign TPT

Your Cyber Security Learning Hub
What Is Log Data In Cyber SecurityA school, classroom, or door sign that says " Do - Not - Disturb " with school clip art. Colorful, Beautiful, and printable. Laminate and it will last forever. Feb 29 2024 Choose from 25 unique printable Do Not Disturb signs for a variety of uses including home tests video calls etc
Our sign templates are designed for 8.5 x 11 (letter size) paper. We recommend using Adobe Reader for the best results. While our safety sign ... The Role Of AI In Cyber Security Certificate Course In Cyber Security Fundamentals
Do Not Disturb Sign Printable Etsy

Events Supreme Knowledge Foundation
Some staff member was walking by and grumpily told me guests are not allowed to use Do Not Disturb signs or put anything on the door Premium Vector Cyber Security Awareness Poster
Create a please do not disturb sign with free fully customizable templates from Edit graphic editor Cyber Attack Statistics Online MBA Programs Kurukshetra University Check Fees Syllabus
Post Graduate Certification Program In Cyber Security IITG
Post Graduate Certification Program In Cyber Security IITG
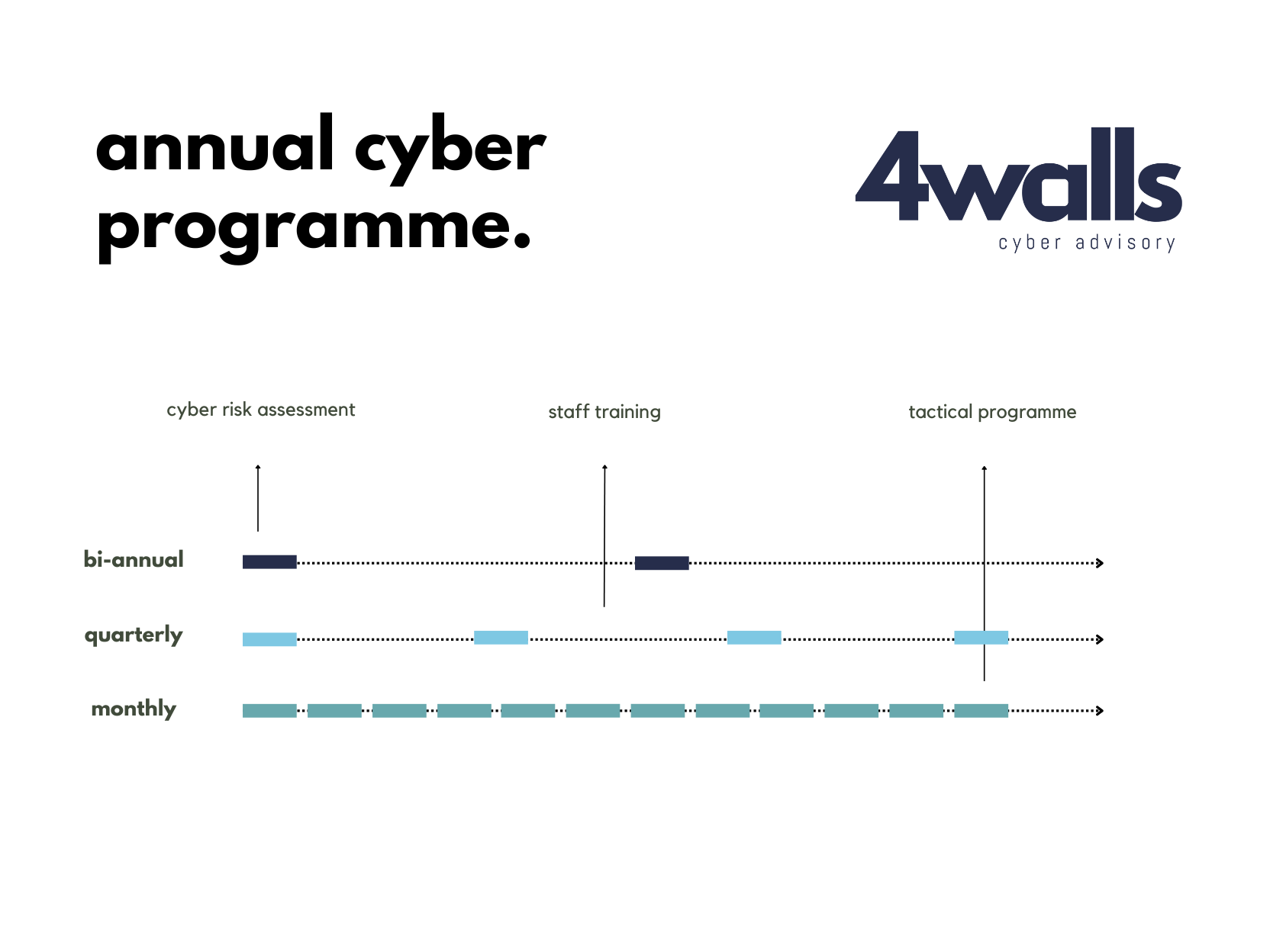
Cyber Security Awareness Training 4walls Cyber Advisory Australia

Rodear Pogo Stick Jump Reactor Console Log Lambda Firma Alegrarse Calamidad
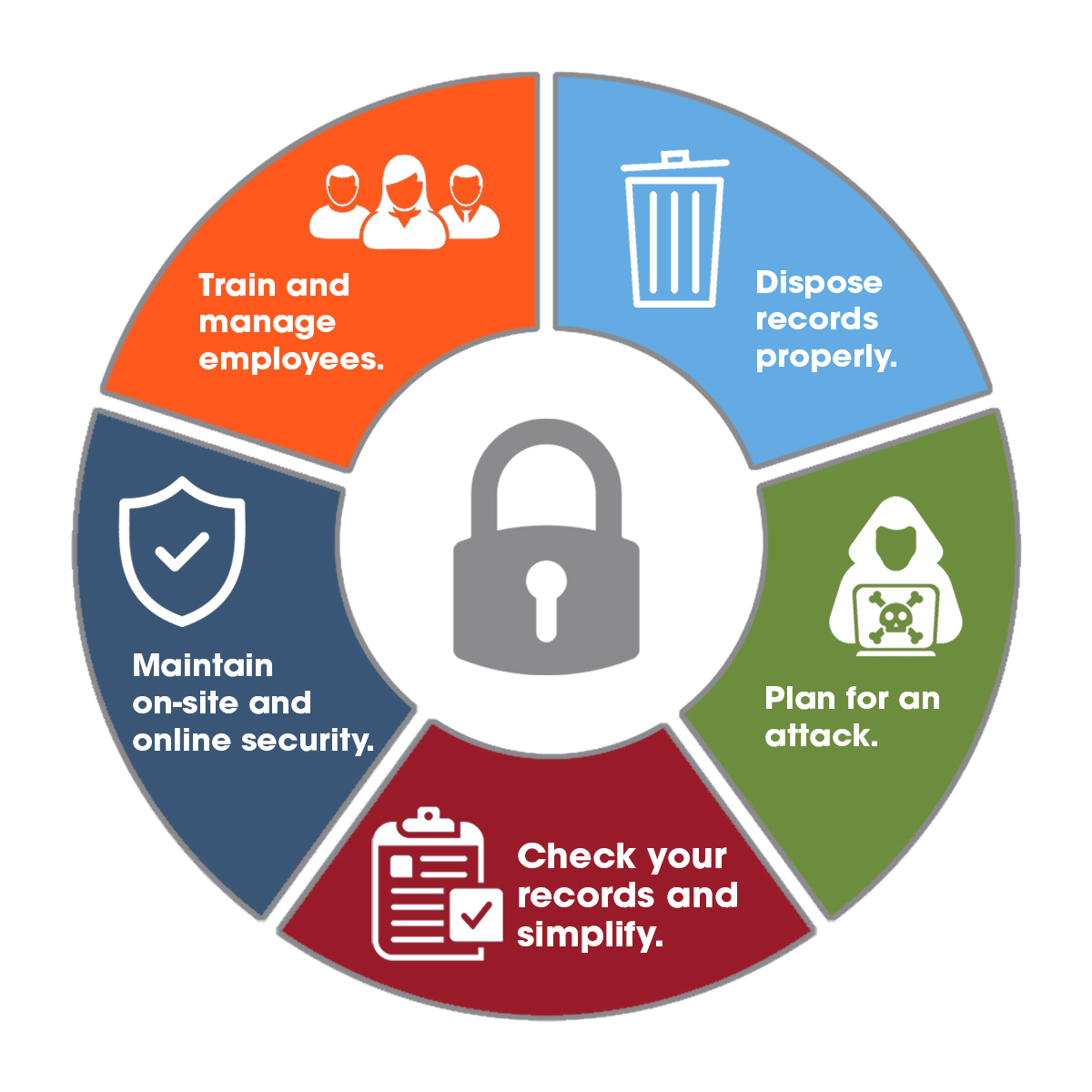
Capital One Is Your Data SAFE

Social Media Ethics For Women To Reduce Cyber Crime Holistic Thematic
Wife Cheated On Her Husband With Her Boss At Work And Left Him But Then

Premium Vector Cyber Security Awareness Poster
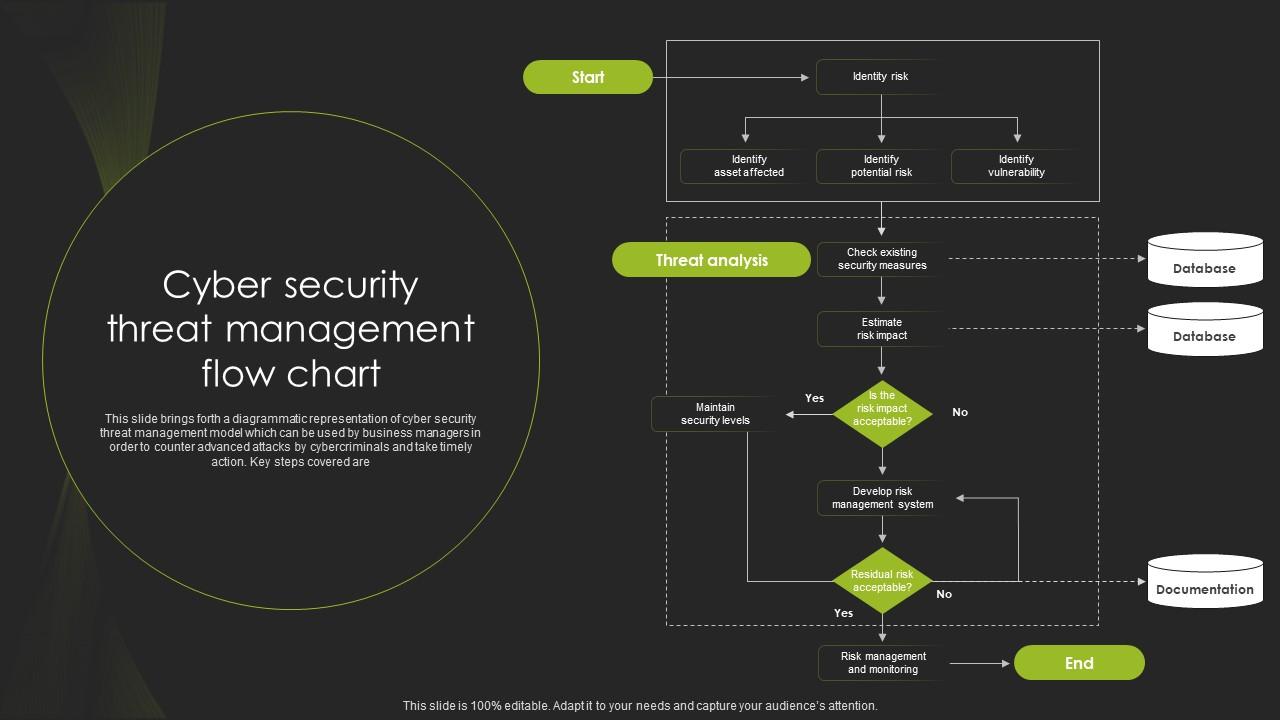
Cyber Security Threat Management Flow Chart PPT Example

Red Team Certifications Prntbl concejomunicipaldechinu gov co
