What Is Sqlmap In Cyber Security are a versatile option for anyone looking to produce professional-quality files swiftly and easily. Whether you need personalized invites, resumes, coordinators, or calling card, these design templates enable you to customize content effortlessly. Merely download the design template, edit it to suit your needs, and print it in your home or at a printing shop.
These themes conserve time and money, offering a cost-efficient choice to employing a designer. With a variety of designs and formats available, you can discover the ideal design to match your personal or company demands, all while maintaining a refined, specialist appearance.
What Is Sqlmap In Cyber Security

What Is Sqlmap In Cyber Security
All California courts use the same basic set of forms for divorce You can find the most commonly used forms on this page Dissolution of Marriage (Divorce) Forms. Dissolution of Marriage with Dependent or Minor Children By Agreement (Packet #15)
Uncontested Divorce with No Children Southern Judicial Circuit

Sqlmap Tutorial Sqlmap Demonstration What Is SQLMAP Live Bug
What Is Sqlmap In Cyber SecurityThese forms are available, by clicking on the links below, in an interactive PDF format, so they may be completed online and printed. How to use the forms Fillable PDF to DownloadBlank PDF to PrintForm 14 If you need additional copies Schedule of Basic Child Support Obligations
We found 6 results when searching for divorce. Category, Form Number, Name, Revised. Civil Forms, Certificate of Divorce, Certificate of Divorce, 3/31/2021. Sql Injection Tool Kali Quickmzaer Cyber Security Audit Template Prntbl concejomunicipaldechinu gov co
Dissolution of Marriage Divorce Forms

How To Use Powerful Sqlmap Kali Linux Hacking Sql Injection Using
Finalize your divorce paperwork If nothing has been filed by your spouse the next step is to complete the form marked 3 Save Form Print Form About Sqlmap Cybr
Blank forms to print and fill out on your own with how to instructions for completing and filing Or use our do it yourself interview program Washington KSEC ARK Pentesting And Redteam Knowledge Base SQLMap SQL Injecton Cyber Security Awareness Month October 2022 National Informatics Centre

15 Cyber Security SQL Injection Using DVWA And SQLMAP Anand K

Sqlmap Sql Injection Picture Templates Wifi Cracker

Cyber Security Domains
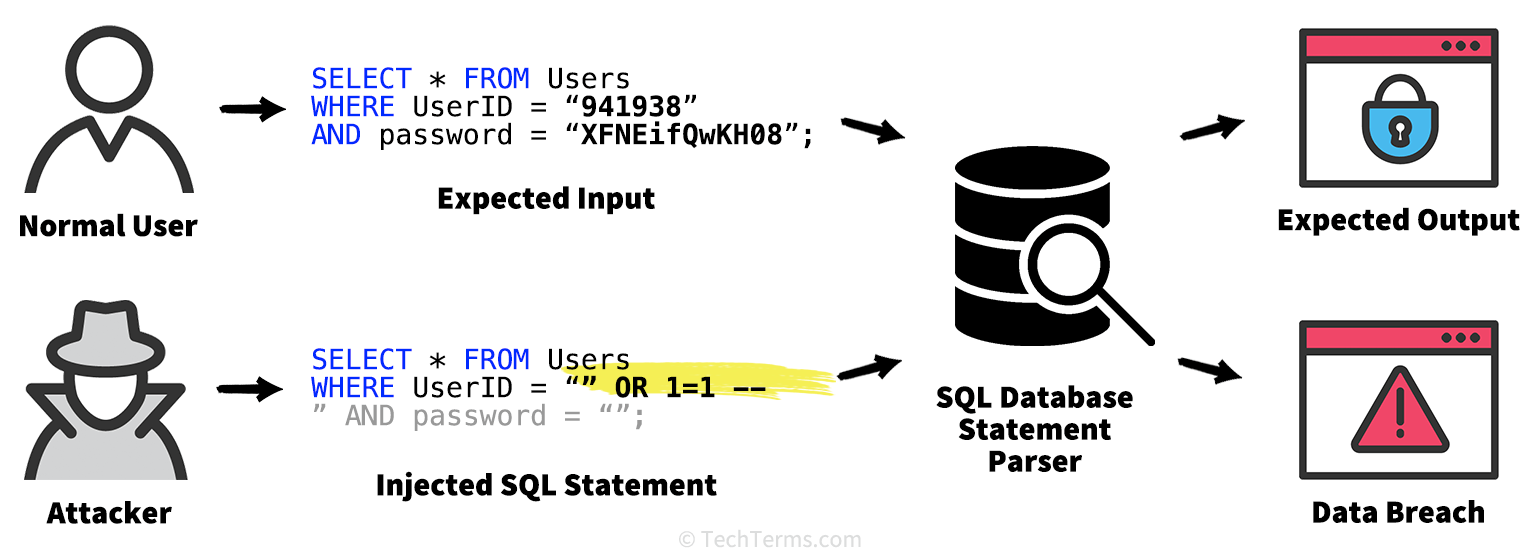
SQL Injection Definition

Proxy Servers SY0 601 CompTIA Security

Official Figures Show Archives TrendRadars

Cyber Attack Wallpaper

About Sqlmap Cybr
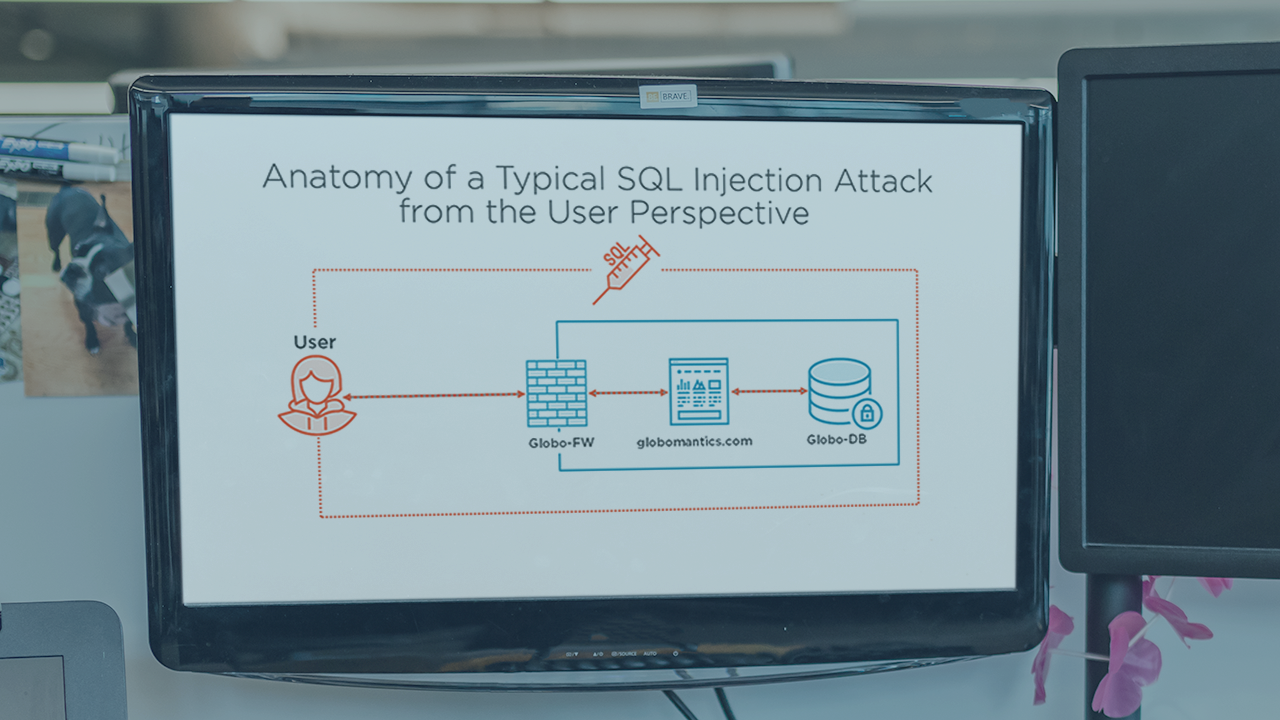
Initial Access With Sqlmap Pluralsight

Sqlmap Cheat Sheet Commands And Flags